
.svg)
.svg)
Originally published by New Context.
For any business that primarily interacts and does transactions with users online, the last thing you want potential or long-standing customers to see when they are trying to connect with you is the dreaded 404 error screen. It is true that in some cases, this error could indicate a problem on the user side. For example, lack of memory or a slow network connection may be the culprit. However, at the other end of the spectrum, this error could indicate that your server is overwhelmed not by actual users, but virtual ones.
Of the many types of cyber threats that your organization may encounter in the cloud, one of the most debilitating is a denial-of-service (DoS) attack. In the most severe scenario—a distributed denial-of-service attack (DDoS)—access denial is extended throughout your network causing multiple web servers to crash. Although DDoS attacks do not typically threaten your data security management, they can have sharp costs of lost time and real dollars. Hence, knowing how to stop a DDoS attack can be a lifesaver for your company.
DDoS attacks are not simple inconveniences. In fact, the loss of time and money can be staggering, as illustrated in the figures below.
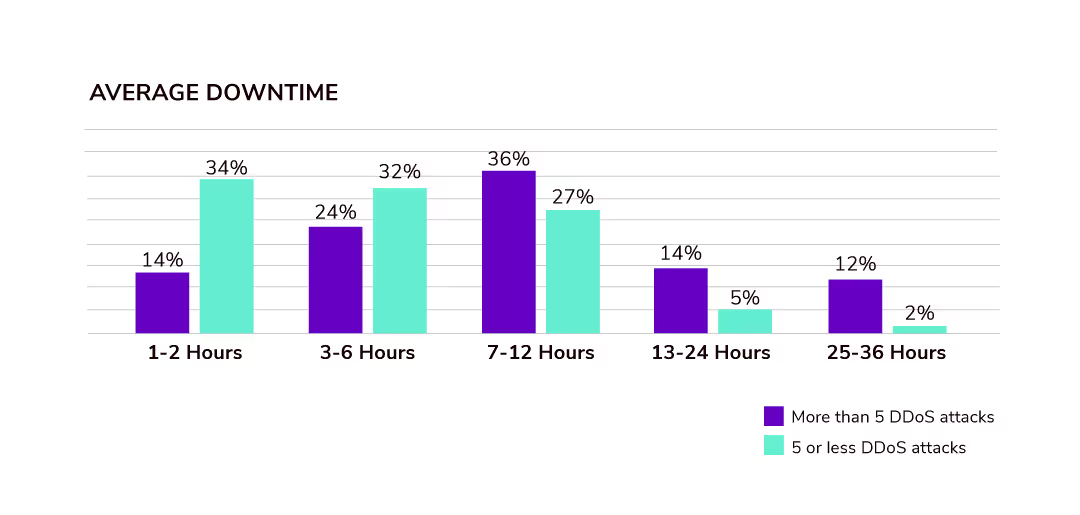
Image Source | A10 Networks
As the graph above shows, DDoS downtime impacts may last for anywhere from an hour upwards to a day and a half for companies that experience five or more attacks.
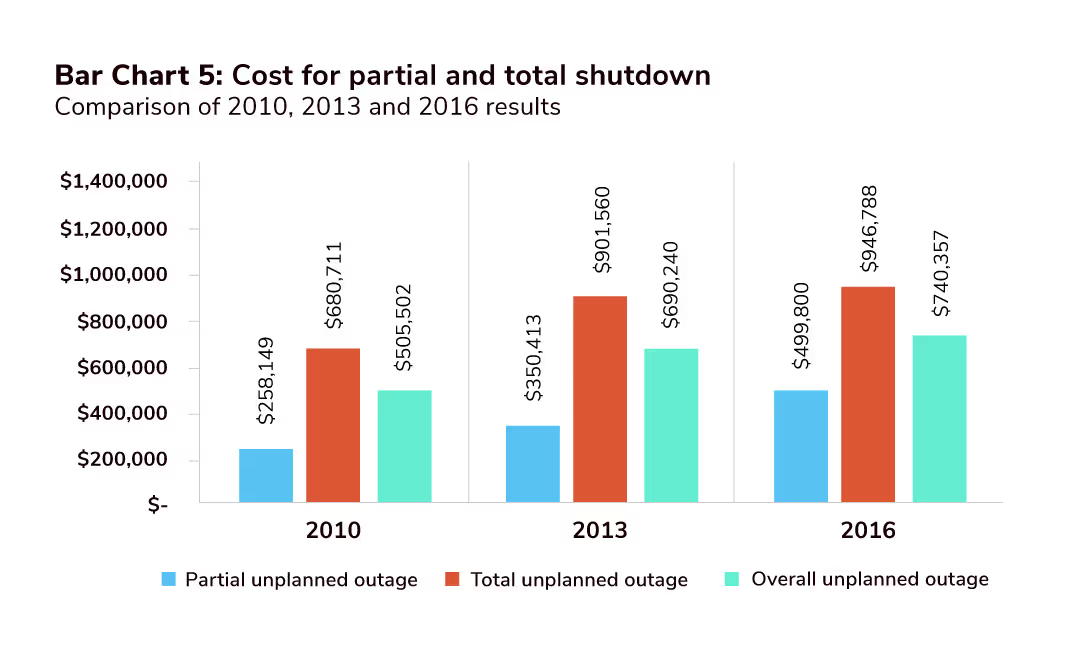
Image Source | A10 Networks
As you can see in the figure above, the cost to businesses for downtime has been on an upward trend. Obviously, these attacks can severely hamper your operations if you are exposed. Not to mention the indirect damage; such as the degradation of your reputation with customers and the general public. Before taking a look at how to best prevent a DDoS attack, let’s explore the different types.
It is not atypical for DDoS attacks to target various aspects of cloud computing deployment in order to take advantage of any vulnerabilities that may exist. The type of attack that you may face could be any of the following:
The perpetrators that use DDoS attacks often target large corporations and governments; however, no one is immune from being a target. Obviously, these attacks can wreak havoc by jamming your communications. The question is how to stop them?

Generally, DDoS attacks are not threats to data or information compromise; however, they can severely hamper one of the tenets of InfoSec—the assurance of data availability when required. So, how do you stop DDoS attacks? Unfortunately, stopping an attack once it has started is almost impossible. Therefore, all efforts should be made to prevent these attacks before they occur. Fortunately, there are the following guidelines that can be successful in achieving this goal:
Incorporating all of the above can help make your application deployment significantly more resilient to DDoS attacks. However, the most important thing to do is to plan for security threats, including DDoS attacks, in all phases of your development and deployment with a trusted security partner.
Explore our DevOps resource library. Level up your Salesforce DevOps skills today.

.avif)


.svg)
